By default, unRAID has a few pretty big security vulnerabilities which should be addressed immediately after installation.
My take is that unRAID is secure enough to operate within my home network behind a firewall, not exposed to the internet. Adding the steps here will make it more secure to protect against the unlikely, yet unfortunate possibility that someone nefarious gains access to your home network.
Here’s my list of steps taken to secure my unRAID install. If folks have more that I’m missing, I’d love to add them here!
Add password for root
It’s really bad that unRAID doesn’t force you to set a root user password as part of the installation. There’s really no excuse for this type ‘insecure by default’ philosophy when it’s so easy to fix.
So, to fix it yourself, go to the web UI and navigate to Users > Select ‘root’ > Add a Password.
It will take all of 30 seconds to do it.
Create users that aren’t root
It’s always a good idea to do as little as possible as the root account on a Linux system. While you’re on the Users screen, go ahead and make users for yourself and others you want to have access to shares. The only thing these users can do is access shares.
Restrict access to your shares
If you don’t have to expose a share via SMB, don’t! Just turn them off.
If you don’t have to give people write access, make them read only.
I prefer to set my shares that are available via SMB to “Private” for the Security level which gives guests no access, and then set the proper access control for each user in the house. To make the changes, just go through each share under the Shares tab and set your SMB Security Settings and User Access however you see fit.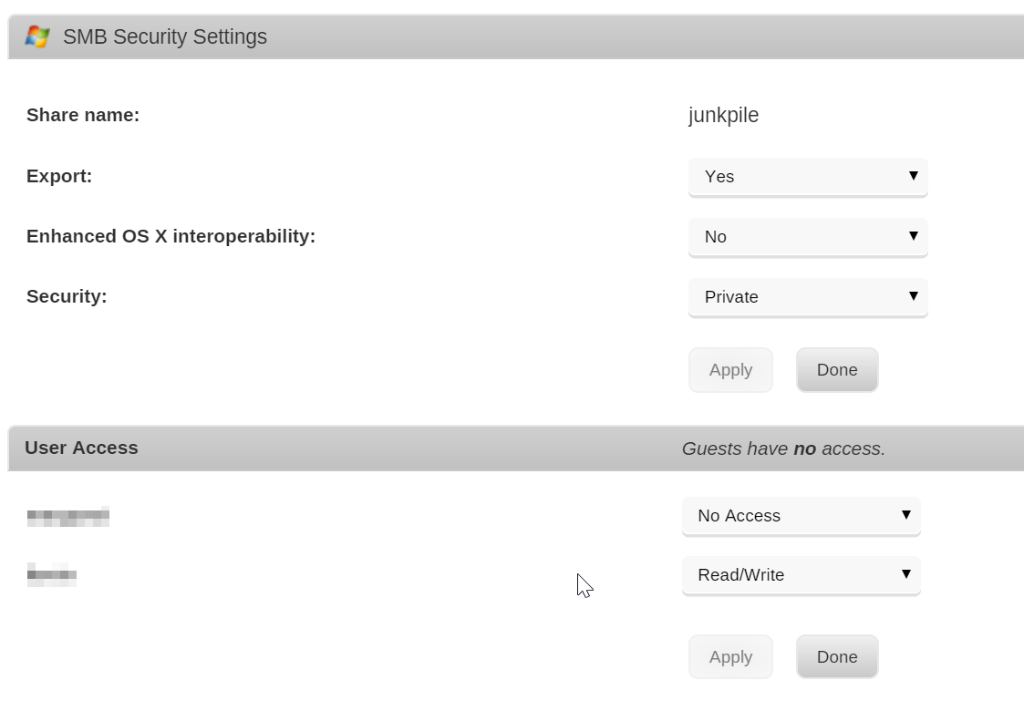
Disable access to the /flash share
For some crazy reason, the USB drive that hosts the operating system is shared by default as /flash. I don’t remember if the default permissions on it are “Private” or not, but I think it’s a good idea to just not have it shared at all.
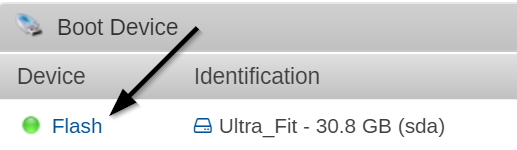
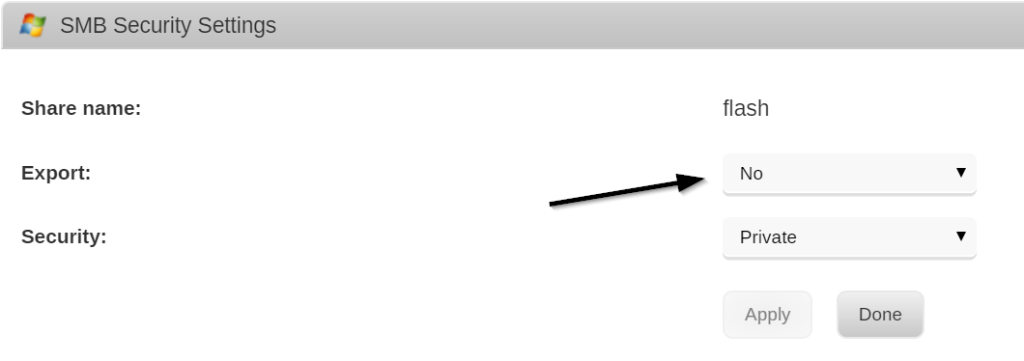
This one is trickier to find, however, because it’s not listed under the Shares tab. To find the controls, go to the Main tab, and click on the Flash drive link.
From there, set the Export to “No”.
Disable SMB1
The folks that built the SMB protocol are serious about telling people to stop using the first version for a variety of security reasons. Now, many of those might relate to Windows-only devices, but there’s no reason not to disable it on your Linux box as well.
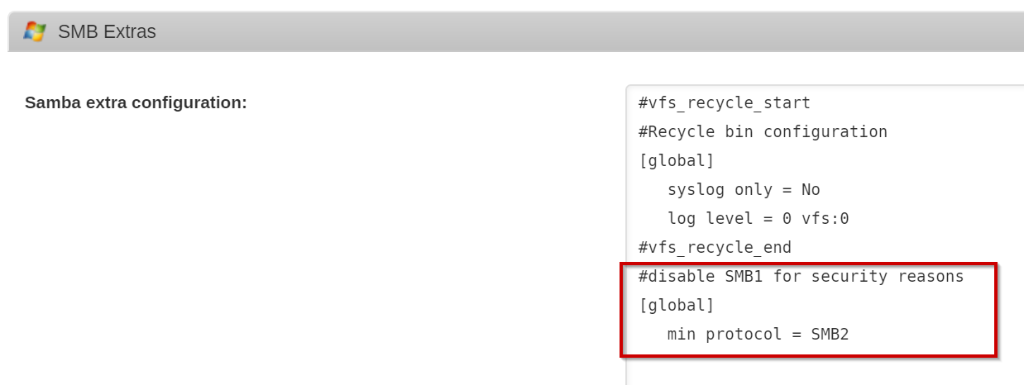
Go to Settings > SMB (Under Network Services). Under the SMB Extras add the following line text:
#disable SMB1 for security reasons [global] min protocol = SMB2
Disable Telnet & FTP access
unRAID comes with Telnet and FTP enabled by default. That’s really pretty silly this day and age. If you want to access a command prompt, you should use ssh. If you want to transfer files, use anything but FTP.
The easiest way to disable them both is to leverage the Tips & Tweaks plugin.
- Install the Tips and Tweaks plugin by going to Plugins > Install Plugin and using the following URL:
https://github.com/dlandon/tips.and.tweaks/raw/master/tips.and.tweaks.plg
- After it’s installed, navigate to Settings > Tips and Tweaks (under User Utilities)
- Find the “Disable FTP Server & Telnet” option and select “Yes”

Fix common problems plugin
This one is nice – it’s basically a health check on the unRAID system. It’ll scan logs, look at your current config, and help you find common problems that you may have overlooked.
You can install it by going to Plugins > Install Plugin and using the following URL
https://raw.githubusercontent.com/Squidly271/fix.common.problems/master/plugins/fix.common.problems.plg
You can learn everything you need to know about the Fix Common Problems plugin on it’s forum thread here.
Ransomware protection
I honestly don’t know if this plugin would help in the event of a ransomware attack, but I think the principle is sound and it’s a pretty low hassle way to add some protection. The recent WannaCry ransomware attack highlighted the need for some additional consideration for me.
The general idea is to create a honeypot of files and shared folders that, if modified, immediately trigger unRAID to go into read-only mode (and/or disable access to all shares). If someone tries to encrypt and delete your files, unRAID would simply cut off access. This is particularly useful since these shares can be accessed by all of your users on potentially vulnerable machines… so if one of their machines gets infected with randsomware, and it tries to access your unRAID shares (because those machines likely have the share passwords cached), unRAID can stop the attack from being completely successful.
You can read all about the Randsomware plugin here on it’s forum thread. To install it, I found it easiest to install the Community Applications plugin and search for it and install it from there.
Setup email notifications
This one is important so that you can be notified by the various plugins and unRAID itself about the condition of the server. This isn’t just about security, obviously, but also about the general health of the system.
For example, you’ll be notified about plugin and server updates which are available, hard drives that are too hot, errors that crop up, etc.
You can find the settings under the Settings tab > Notification Settings
Keep your server up to date
unRAID itself and all of the plugins are easy to update – just go to the Plugins tab and click the “Check for Updates” button. Then go through and update each plugin – including the unRAID OS itself.
If you run any Docker containers, unRAID will let you know if they have updates available as well on your dashboard (they’ll be a different color). For any VM you run, make sure to check for updates on them regularly as well.
Further Reading
There’s a good thread on the Lime Technologies forum – Is unRAID really unsecure? I would recommend reading that as well – there are some good pointers there about other basics not covered here, like making sure to keep your system up to date, maintaining good backups, etc.
My take is that unRAID is secure enough to operate within my home network behind a firewall, not exposed to the internet. Adding the steps above make it even more secure to protect against the unlikely, yet unfortunate possibility that someone nefarious gains access to your home network.
Thanks!
3 years later and same basic issue.
I just bought Unraid, so obviously I can accept the way Lime has done the defaults since I know the workarounds, but the defaults aren’t an issue for users like us. It’s an issue for the people who haven’t been using Linux as a SMB host for 20+ years and don’t know some of the gotchas.
I got pointed here by a thread on the Unraid forums and one of the Lime official responses was that it was set up this way because Unraid is an appliance. Anyone remember the Cobalt appliances of the late 90s / early 2000s? Yeah. I do. Worked there. We knew how to make web processes run as a different user and to avoid root owning too many files, as well as file permissions. “Appliance” doesn’t HAVE to mean insecure. It’s a little more hassle for the dev team to build it right but once done … it really isn’t a problem. My guess is Lime doesn’t want to change the basic paradigm that they’ve had since v1 but that just lets the problem cascade.
And the “an Appliance” line is misleading. Lime KNOWS many of their users are making these servers available to the broader internet. Locking down via services can do a world of good, but having basic security on the system to begin with is a better place to start.
I’m with you. I’ve been complaining about the same shitty bug with NFS for years now and it looks like it only *just* got fixed. The bug would kill Fuse when trying to delete a large number of files via an NFS share, but since “nobody” uses NFs, nobody cared to fix it (despite being told by the owner of LimeTech that “time would be put into it immediately”). And don’t even get me started on the “support” you get for your money.
If there was a good alternative I would’ve ditched unRAID long ago but Docker support just isn’t good enough on any of their competitors.
PS. The Ransomware plugin mentioned is deprecated these days, meaning new installs can’t use it. Just to save time for anyone else who happens to find the article.
Hi Kevin. This is a helpful post and the first thing I checked after my initial unraid setup. Appreciated
If you want some ransomware protection in 2020 see here: https://forums.unraid.net/topic/93965-script-binhex-no_ransomsh/